All this process has been a great learning for me and that's why I decided to document it. Connecting your node isn't (yet) that intuitive as it should, to auto withdraw your sats and use SN in a fully noncustodial manner. Consider this just a reference, it's generic due to my current tech skills did not enable me to cover all scenarios, so many things will not exactly match your case as it will be mostly depending on your node OS implementation. However, hope you'll find the following steps useful.
0. Open a channel with SN node
This is not mandatory, but it will definitely help the autowithdraws to find a cheaper and faster path toward your node.
pubkey: 03cc1d0932bb99b0697f5b5e5961b83ab7fd66f1efc4c9f5c7bad66c1bcbe78f02
connect via IPv4 on clearnet:03cc1d0932bb99b0697f5b5e5961b83ab7fd66f1efc4c9f5c7bad66c1bcbe78f02@52.5.194.83:9735
connect anonymously via Tor03cc1d0932bb99b0697f5b5e5961b83ab7fd66f1efc4c9f5c7bad66c1bcbe78f02@xhlmkj7mfrl6ejnczfwl2vqik3xim6wzmurc2vlyfoqw2sasaocgpuad.onion:9735
via terminal:
lightning-cli connect <node_id> <ip> [<port>] lightning-cli fundchannel <node_id> <amount_in_satoshis>
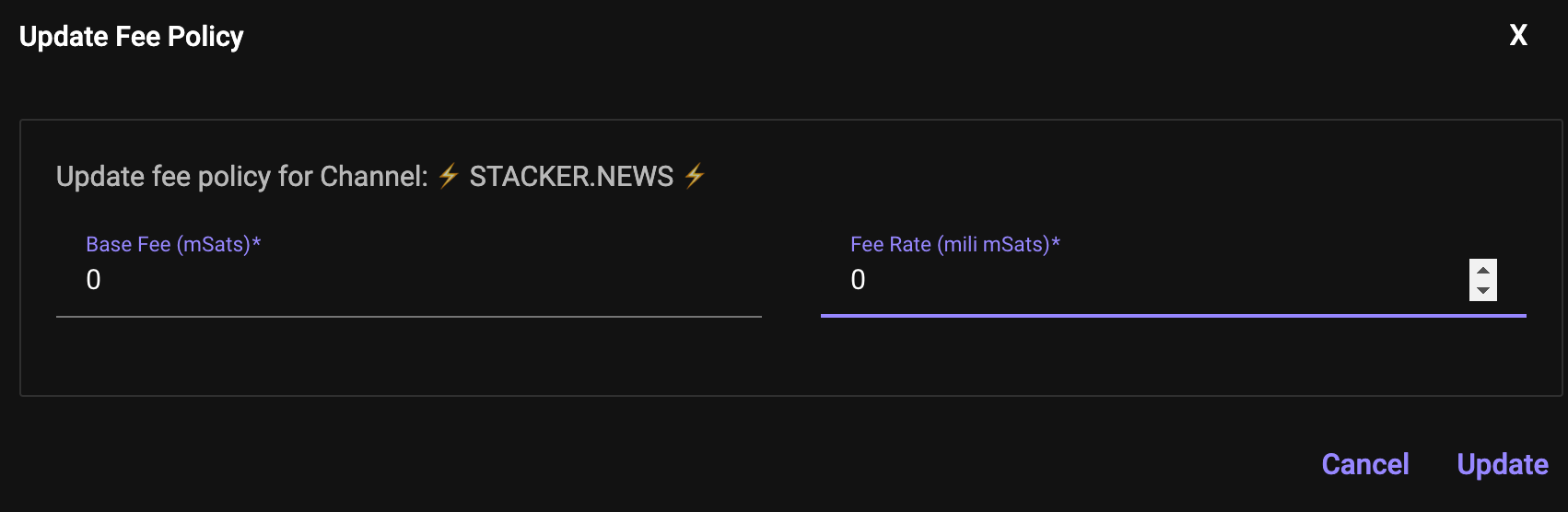
It could also be a private channel and this will allow you to use it exclusively for your autowithdraws and get the cheapest and faster transaction ever setting
Base Fee (mSats) and Fee Rate (mSats) equal to zero. By command line should be something like (depending on which node OS you are running):lightning-cli setchannel <channel_id> <base_fee_millisatoshi> <fee_per_millionth>
<base_fee_millisatoshi>: This is a fixed amount of satoshis that will be charged for every payment routed through your channel, regardless of the payment's size.<fee_per_millionth>: This is a variable fee represented in millionths of a satoshi per satoshi routed, essentially a percentage of the transaction amount.... or you could also easily use Ride The Lightning in case you have it installed:
1. Get your rest host and port
2. Get your invoice only rune
method=invoice.So it's now time to open the terminal in your device and connect to your node via ssh, usually something like
ssh user@node.local, and then run the following command to generate one:lightning-cli createrune restrictions='["method=invoice"]'
It's useful to verify the rune has been correctly created, verifying the list of existing rune running the following command:
lightning-cli showrunes
You can see all official documentation about
lightning-commando-rune from here.3. Get your cert
sudo nano ~/core-lightning/data/c-lightning-rest/certs/certificate.pem
Make sure the path is correct, and, if it's, you should get a new window with the certificate. This certificate is encoded with base64, copy it and make sure you remove all spaces before pasting it to the SN form.
4. Set your desired balance
Last values to set are the desired balance to be left on SN wallet and the maximum fee as a percent of the withdrawal amount. I assume that if a channel is set toward SN node (as explained in step 0) we can also set zero here. I decided to set 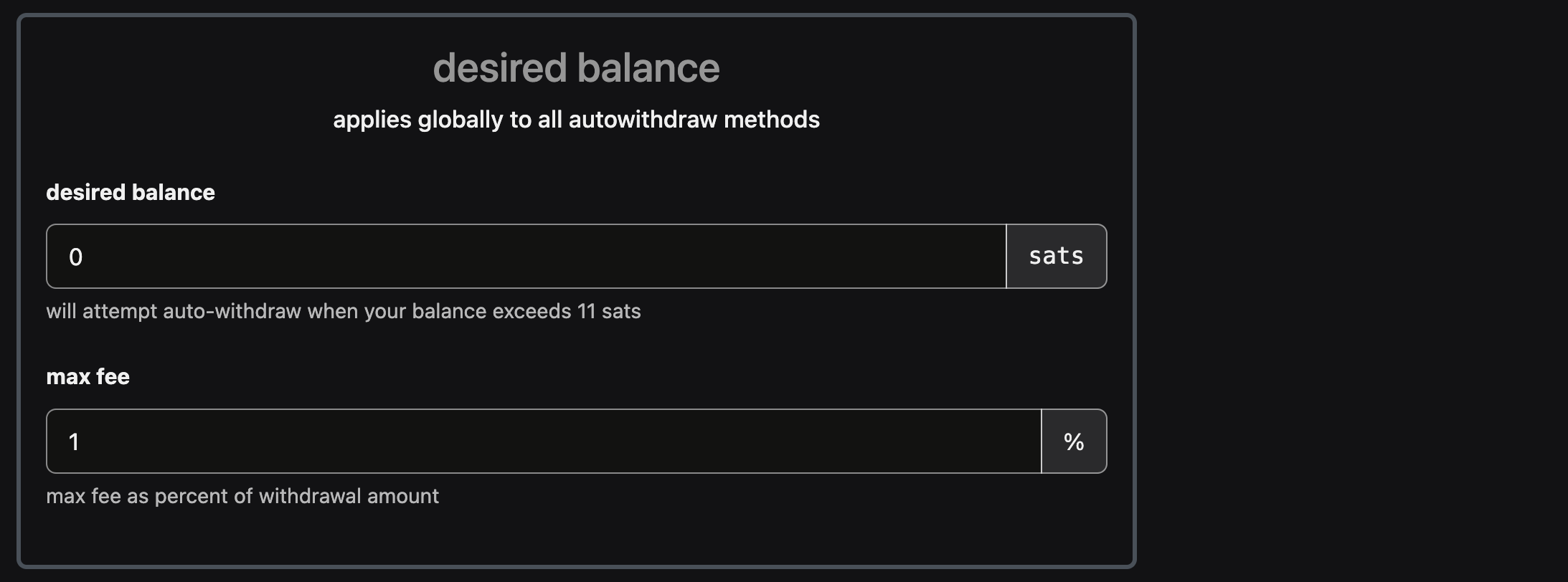
1 just in case. I also set zero on desired balance because I do not want SN to be a wallet, but just an app I use to share and learn.
5. Attach and troubleshoot
Hitting the attach button will submit the information attached in the form. When using Tor, it could take a bit, so be patient and wait for the outcome to appear in the  In my case, still have unsuccessfully completed the goal, so my CLN node is not yet attached due to an error:
In my case, still have unsuccessfully completed the goal, so my CLN node is not yet attached due to an error:
log section below.
21m [cln] ERROR could not connect to CLN: request to https://hidden.onion:2104/v1/invoice failed, reason: write EPROTO C077EC2F067F0000:error:0A00010B:SSL routines:ssl3_get_record:wrong version number:../deps/openssl/openssl/ssl/record/ssl3_record.c:354: 21m [cln] ERROR failed to attach wallet
I'm not sure if I am doing something wrong, or if the Tor connection is maybe so unstable that give me this error... Anyway, ideally, I'm still waiting for @k00b and @ek to confirm what's going on from @SN side. If you have a CLN node and want to play around, head to wallet > attach wallets > CLN and try to connect your node.
It will be nice if you can comment below your experience attaching your CLN node, either via clearnet or tor, so it might help better understand and learn how to correctly achieve this goal!
certificate.pemin a directory dedicated to the CLNRest plugin. Which CLN version are you running? It seems like you are not running at least v23.08 since CLNRest is a built-in plugin from this version on. It then stores the certificates at$HOME/.lightning/mainnet/.1certificate.pemis ambiguous since there should also be a server certificate in the same directory. In v23.08, the certificate we need is calledca.pem. It's the certificate of the certificate authority (CA) which establishes the trust chain, commonly called root certificate (yes, SSL/TLS is confusing).xxd -p -c0 ca.pemto get it in hex. My CA certificate starts with-----BEGIN CERTIFICATE-----which means it's not base64 or hex. Is this not the case for yours?Footnotes
23.08-hotfix-1so it should have CLNRest as built-in. And here's the path~/core-lightning/data/c-lightning-rest/to thecertificate.pem1. Also tried to find theca.pemyou mention without success, the only files found in the same folder areaccess.macaroon,certificate.pem,key.pemandrootKey.key. Any other place I could look for this file?-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----making sure I removed any space between the characters, converted to base64 using an online converter and then inputting in the form everything as a single line.http://to the onion address, the input validation script obviously give me error instantly: so are you saying I should run CLNRest over HTTPS? How I can do that?Footnotes
method=invoice. We then use this rune with theRuneheader as mentioned here and as you can see here. We don't do anything else to it.invalid json response body at http://hidden.onion:2104/v1/invoice reason: Unexpected token < in JSON at position 0means that we connected to your node successfully but it didn't return JSON as expected.cURL? Try this:--clnrest-portduring start to enable it which they don't.command:for example: